Register
FIDO Register allows users to securely register both their unique fingerprint patterns and a confidential passkey.
How to Setup
1 Navigate to Workspace > Workflows, and click on the flow created for FIDO Register. If you need understanding in creating a workflow, refer to the step-by-step guide here.
2 Hover over the plus (+) symbol and select Workflow. From the list, click FIDO Register to add it.
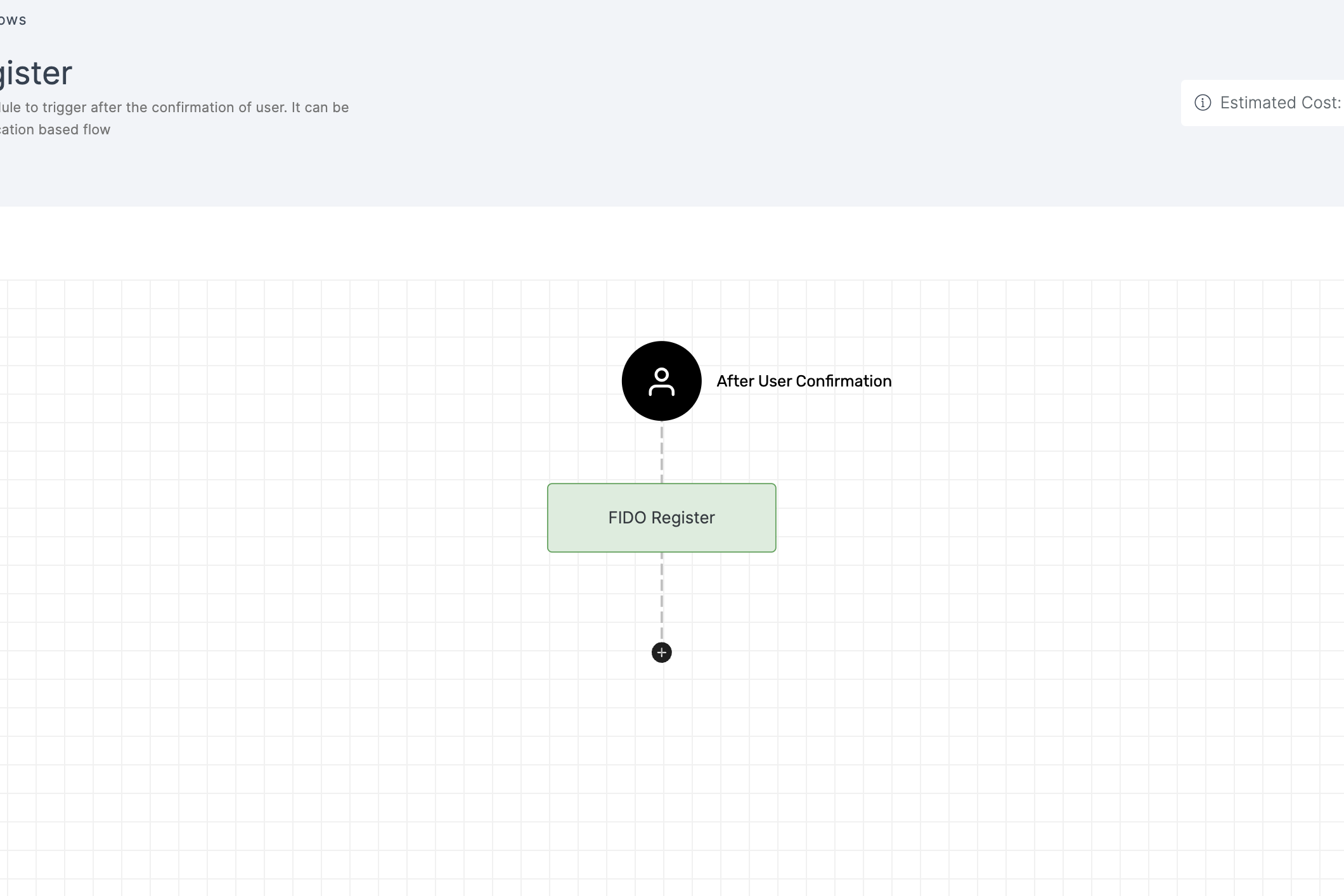
3 Click on the newly added workflow, then select the General tab to customize your preferences.
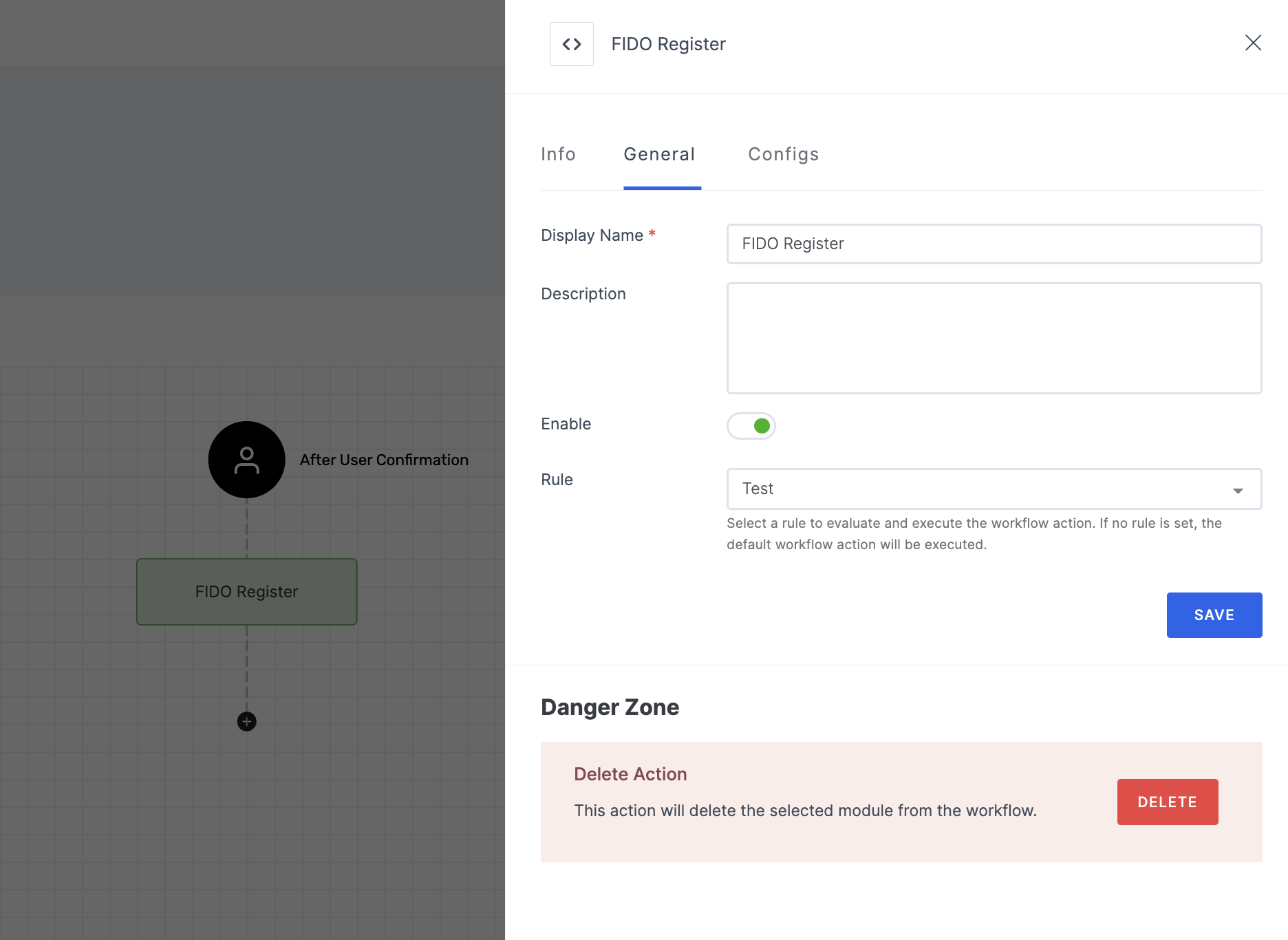
Manage General
(*) Indicates an action to be mandatory.
| Name | Description |
|---|---|
| Display Name* | Set a name to the workflow for easy identification. |
| Description | Summarize the purpose and functionality of this workflow module. |
| Enable | This toggle is enabled by default. When enabled, the particular workflow module begins its execution. Conversely, if disabled, the workflow module remains inactive and won't proceed. |
| Rule | This determines the criteria for triggering the particular workflow module. When the selected rule is evaluated, and is satisfied, the workflow proceeds as provided. If not, the workflow will not be executed. Note: If no rules are set, the workflow defaults to its standard action without any rule. For more information about the rules, refer here. |
4 Then, click on the Configs tab to set the necessary configurations.
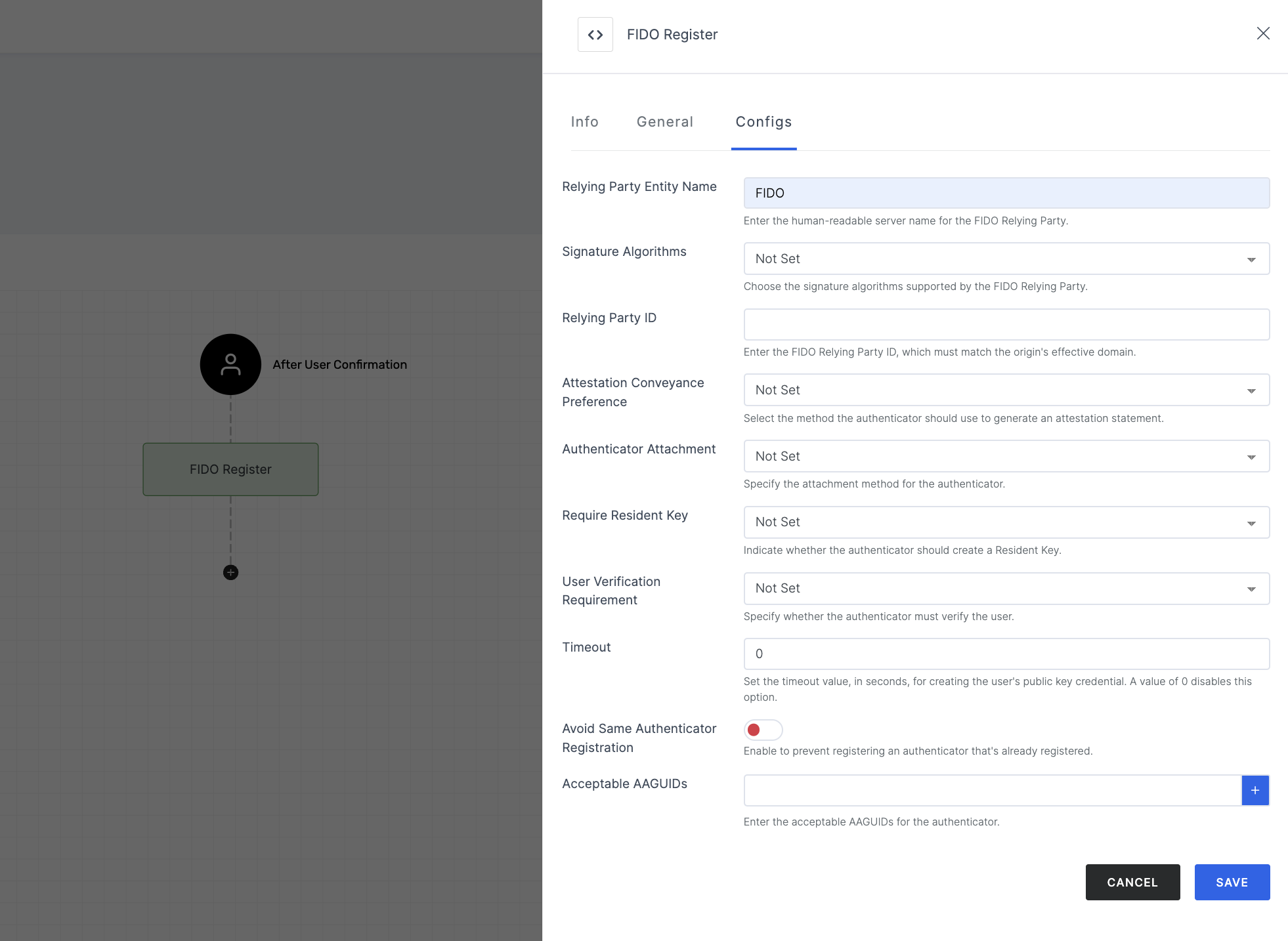
Manage Configs
| Name | Description |
|---|---|
| Relying Party Entity Name | Use a human-readable server name as the FIDO Relying Party. It helps users identify the server or service. |
| Signature Algorithms | Assign specific algorithms used for cryptographic signing to ensure secure communication between the client and the server. |
| Relying Party ID | The Relying Party ID (RP ID) serves as a unique identifier for the FIDO Relying Party and should correspond to the effective domain of the origin. This ID helps in identifying the entity that is requesting the verification. |
| Attestation Conveyance Preference | Attestation statements are used to verify the authenticity of the verification device and can be configured to provide varying levels of detail and privacy. This informs the system about the preferred method for generating an attestation statement. |
| Authenticator Attachment | This conveys a permissible attachment pattern. |
| Require Resident Key | A Resident Key is stored on the verification device itself, allowing for credential storage and management directly on the device rather than on the server. It determines whether a public key credential should be created as a Resident Key. |
| User Verification Requirement | Instructs to confirm the verification of a user. |
| Timeout | Sets the maximum time, in seconds, allowed for generating a user's public key credential. This ensures the process completes within a reasonable timeframe. If set to 0, there is no timeout applied, and the process will wait indefinitely. |
| Avoid Same Authenticator Registration | Prevents the registration of a workflow that is already in the system. |
| Acceptable AAGUIDs | Lists the Authenticator Attestation GUIDs (AAGUIDs) that are acceptable for registration. This setting ensures that only recognized and trusted authenticators can be registered, enhancing security by avoiding the use of unverified or duplicate authenticators. |
5 After you've configured everything needed, click on the SAVE button.
6 Proceed to attach the workflow to the relevant application for execution. Refer to the instructions on how to attach a workflow to an application here.
Expected Result
Based on the provided configuration, the information that will be fetched for FIDO Register includes the following parameters:
| Name | Description |
|---|---|
fido_registered | This indicates whether FIDO registration has been completed. The value will be "True" if the registration is successfully completed and "False" if it is not. |
allow_new_device | Indicates whether a user is permitted to access the service or application from a new or unrecognized device. If set to true, the user can use a new device; if false, the user may be restricted to previously authorized devices. |
fido_registered_at | This provides a timestamp, in Unix epoch format, indicating the exact time when the FIDO registration was completed. This allows you to know precisely when the registration event occurred. |
The response received will include the accurate information mentioned above. Note that, the response values can vary depending on the specific workflow modules.
How it Works
1 Launch Postman or your preferred API tool and execute the flow by configuring the suitable Method, URL, and Body settings. If you're seeking guidance on how to perform these actions, see here.
2 Upon initiating the API call, a verification request will be sent to your configured Verification Way settings.
3 Based on the request, execute the flow in an incognito browser and follow the prompts to complete the verification process.
4 Begin by granting permission to your device and proceed to execute using Fingerprint or Password.
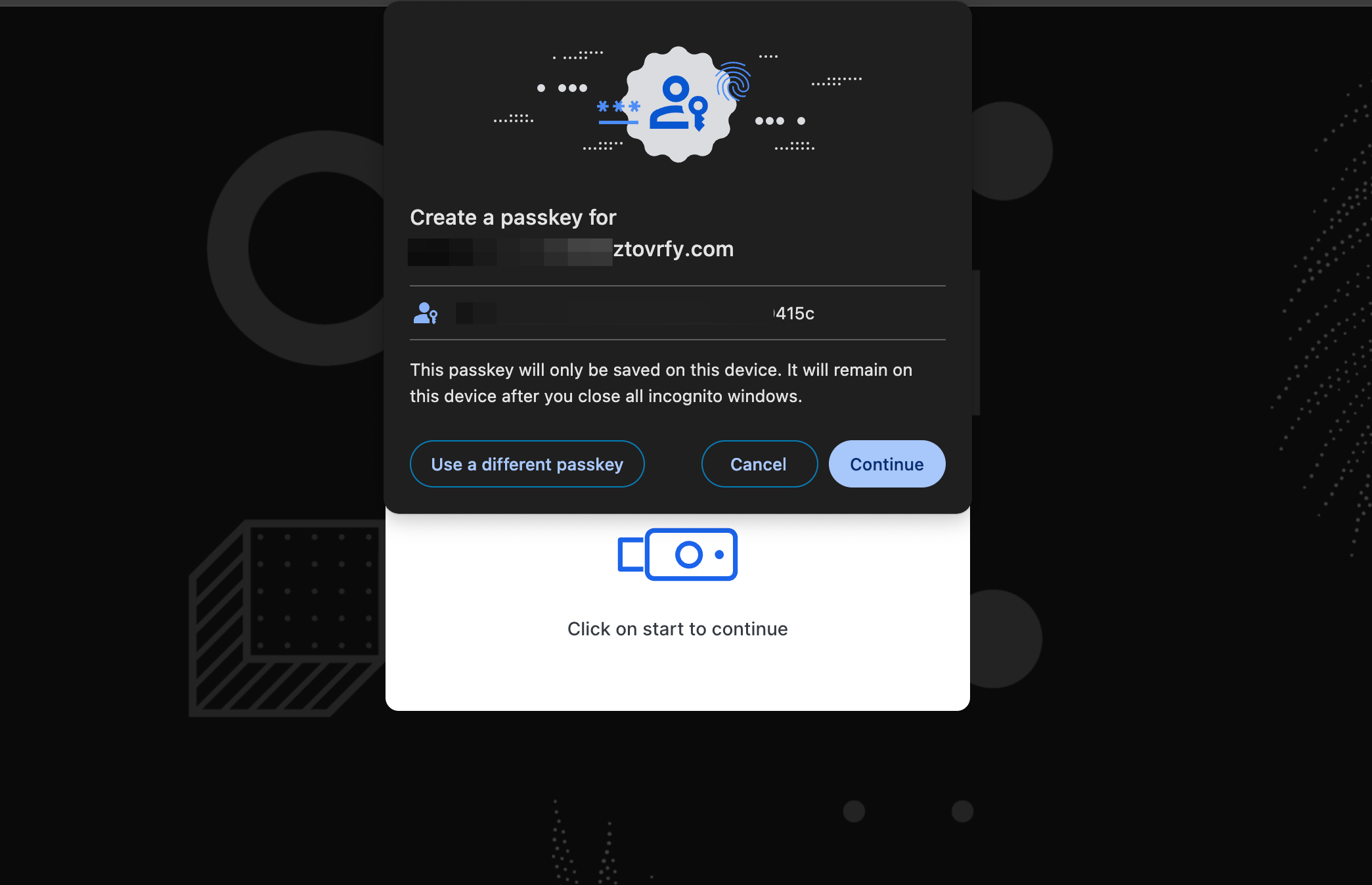
5 The verification process will be completed if the provided data is valid.

6 The response can differ depending on the chosen Verification Way and Notification Way configurations. To know more, see here.
7 Here is a sample response for FIDO Register:
{
"request_id": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxx",
"user_id": "mark@gmail.com",
"workflow": "verification",
"fido_registered": "true/false",
"fido_registered_at": "1719569072",
"allow_new_device": "true/false"
}