Decrypt Response
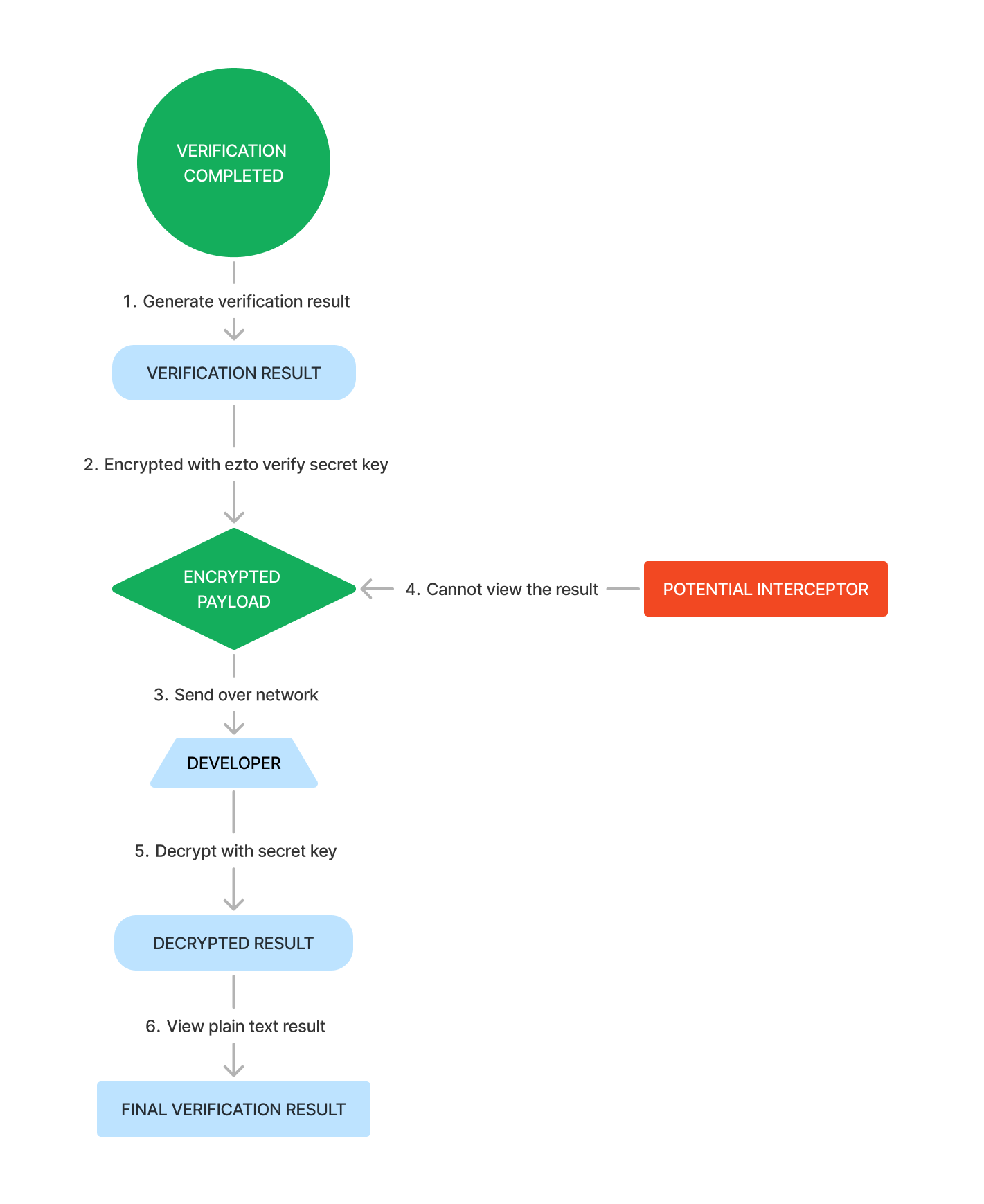
Decrypting a response ensures that the data received in an encrypted format can be converted back into its original, readable form. Only authorized parties with the correct decryption key can decrypt the data, ensuring that it remains protected from unauthorized access.
To help visualize this process, the following flow diagram provides an overview of how decryption works.
Access Application
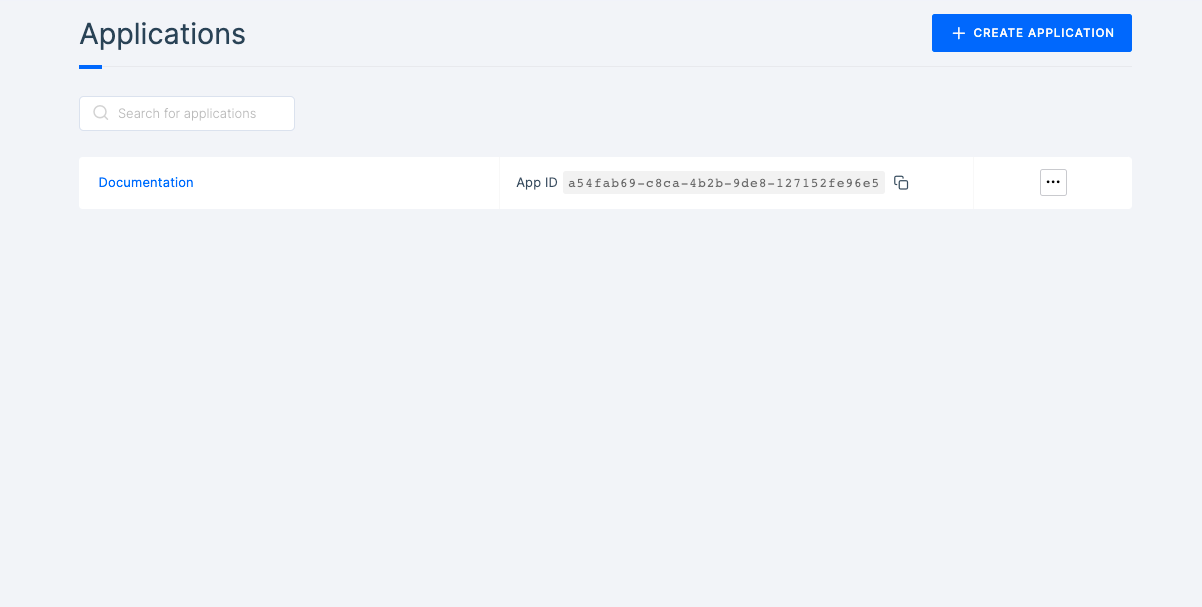
1 Navigate to Workspace, and click on Application.
2 This will take you to the list of all applications available in your dashboard.
3 Click on the application you wish to view enable encryption. This will open the application General page.
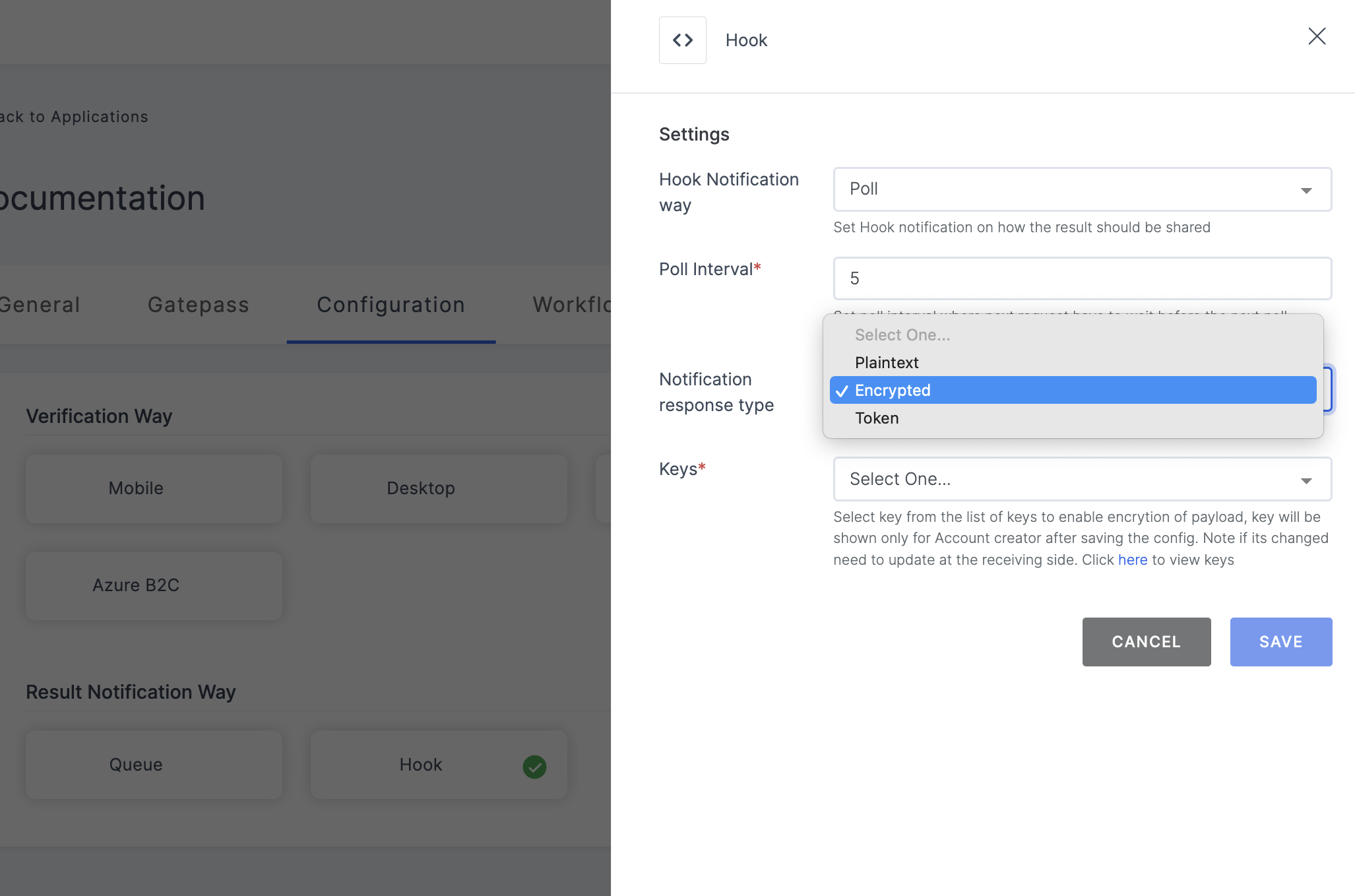
4 Within the application's General page, click on the Configurations tab.
5 Choose Hook for Result Notification Way, and select the response type as Encrypted.
Decrypt Response
1 Choose Encrypted and select the AES key which will be available in the dropdown. To know how to create a Key, see here.

Make sure your required workflow is set before starting with the execution process in order to get the expected result.
2 After choosing the AES key, the Secret Key will be displayed. Copy this key to your clipboard.
3 To initiate the execution process, launch Postman or your preferred API tool and trigger the Send Request API by configuring the suitable Method, URL, and Body settings. If you're seeking guidance on how to perform these actions, see here.
To view result,
1 After completing the verification process, view the exact response with Get Result, and input the copied auth_req_id (from the API request made prior to this) in the request value.
2 Proceed by initiating the API call, once the request is made, you'll receive the response in an encrypted data.
Here is an example of how the encrypted data will appear:
{
"data": "T3vY1#rF9p%hK6m^L4n2wQ*X$8D0a7@N3&sY4!uG5j$9vZb@WqL5oJ8cR2bZ4dP9fE7qK1yM8sU3tV6nW9jX2mQ5rA4nF1vC6hL3kP7oD2D0a7@N3&sY4!uG5j$9vZb@WqL5D0a7@N3&sY4!uG5j$9vZb@WqL5oJ8cR2bZ4dP9fE7qK1oJ8cR2bZ4dP9fE7qK1"
}
3 Now, with the available libraries, use the above copied Secret Key to decrypt the data. Ensure that the same key size is used as the selected AES key. (use the same padding as used in encryption)
Here are some AES libraries
4 Upon performing the decryption of the data, the final response will be displayed.
5 Below is a sample decrypted response:
{
"request_id": "c504a110-c984-4fad-84d7-40dd2c9b082c",
"email_verified": "true",
"user_id": "mark@gmail.com",
"workflow": "verification",
"email_verified_at": "1708757480",
"email": "mark@gmail.com"
}