Tokens
Token is a way of granting access to the users or an applications. This token serves as a ticket to access specific resources or perform certain actions within the application. It's like receiving a special pass once you've confirmed who you are, allowing you to enter and interact with the system without needing to provide your credentials repeatedly.
1 Go to Dashboard > Settings.
2 Click on Tokens.
Tokens have a limited lifespan and may need to be refreshed or renewed periodically to maintain sessions and actions.
Configuration
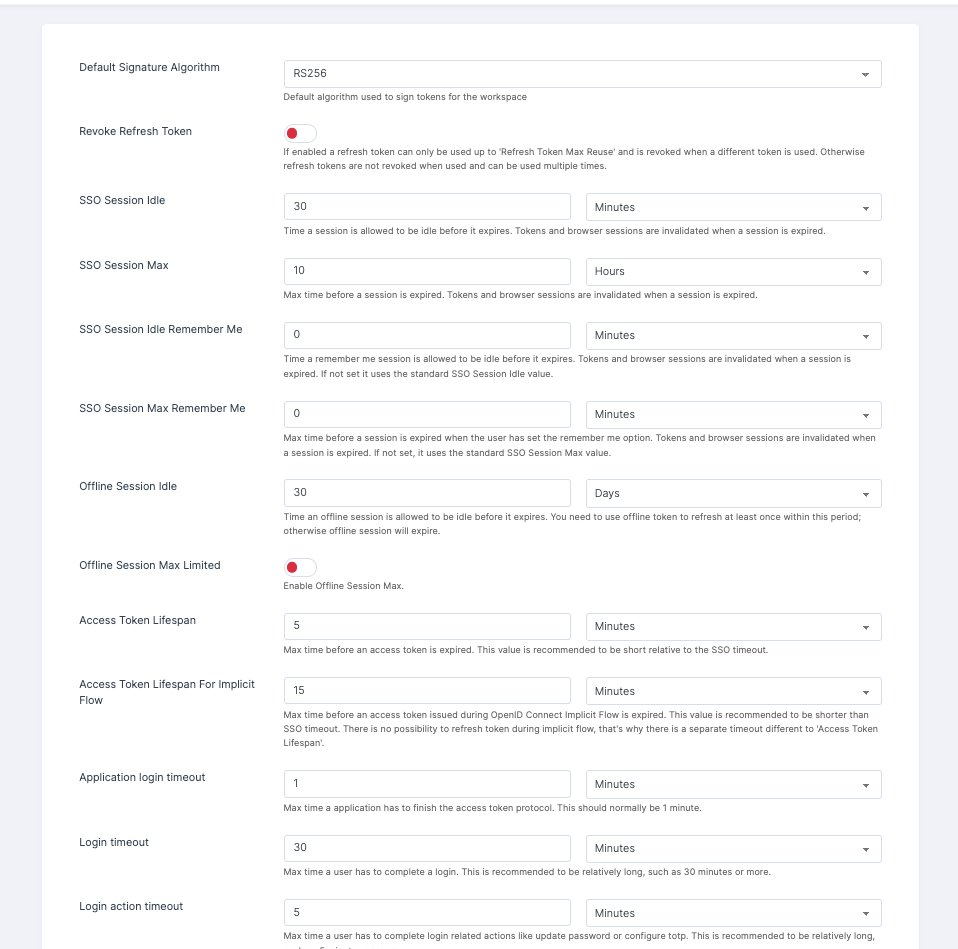
Default Signature Algorithm: The Default Signature Algorithm refers to the standard algorithm used to create digital signatures when no specific algorithm is selected. You can predefine a method for generating a unique digital signature that can be used to verify the authenticity and integrity of digital data.
Revoke Refresh Token: A refresh token is revoked when it becomes useless or invalidated before its scheduled expiration date. In token-based authentication, a refresh token is often used to receive new access tokens without asking the user to enter their credentials.
SSO Session Idle: To specify the duration after which tokens and browser sessions should expire due to inactivity when the application is left idle, you can configure the idle timeout settings.
SSO Session Max: You can configure the maximum duration for a session to expires while using, resulting in the invalidation of tokens and browser sessions.
SSO Session Idle Remember Me: You can set a specific time duration for the SSO Session Idle Remember Me feature after the application is left idle. When a session expires, tokens and browser sessions are invalidated. If no duration is specified, the standard SSO Session Idle value is used.
SSO Session Max Remember Me: Configure the maximum time to remember the user while using the session. Tokens and browser sessions are invalidated when a session is expired. If not set, it uses the standard SSO Session Max value.
Offline Session Idle: To specify the duration after which tokens and browser sessions should expire due to offline session in the application is left idle, you can configure the idle timeout settings as per the need.
Access Token Lifespan: It is recommended to set a configuration for the access tokens, ensuring they expire before the SSO timeout.
Access Token Lifespan For Implicit Flow: The maximum duration configuration before an access token issued during the OpenID Connect Implicit Flow expires should be shorter than the SSO timeout. It is important to note that there is no option to refresh the token during implicit flow, hence the need for a separate timeout distinct from the Access Token Lifespan.
Application login timeout: Configure the time for the Application login timeout. The recommended timeframe for an application to complete the access token protocol is typically one minute.
Login timeout: The time duration to complete the login. Set a relatively lengthy duration, such as 30 minutes or more, for the Login timeout.
Login action timeout: It is recommended to provide users with a relatively generous timeframe, such as 5 minutes or more, to complete login-related actions such as updating passwords or configuring TOTP (Time-based One-Time Password).
User-Initiated Action Lifespan: Maximum time before an action permit sent by a user (such as a forgot password e-mail) is expired. This value is recommended to be short because it is expected that the user would react to self-created action quickly.
Default Admin-Initiated Action Lifespan: The expiration time for an action permit sent to a user by an administrator is recommended to be long. This allows administrators to send emails to users who may be currently offline. However, it is important to note that the default timeout can be overridden immediately before issuing the token.
Override User-Initiated Action Lifespan: You can customize the maximum expiration time for an action permit sent by a user, such as a forgot password email, for a specific action, it is recommended to set a short duration. This recommendation is based on the expectation that the user would promptly respond to self-created actions.