Azure B2C
Azure B2C is a cloud identity management service that enables you to customize and control how customers sign up, sign in, and manage their profiles when using your applications.
Every application execution requires an Onboarding and Verification workflow. The onboarding workflow (can be any) will be used for a new user. You can configure it as "None" for a user who has already been onboarded. Please note that selecting the "None" option for the onboarding workflow will automatically redirect the user to the verification workflow, irrespective of the users availability.
Access Application
1 Navigate to Workspace, and click on Applications.
2 Choose the application you wish to execute the flow with configuration as Azure B2C.
3 Click on the Configuration tab, and select Azure B2C in the Verification Way.
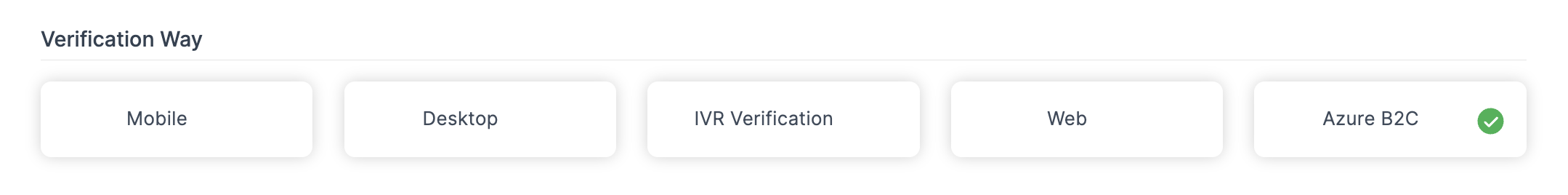
4 You will be displayed with the Azure B2C settings.
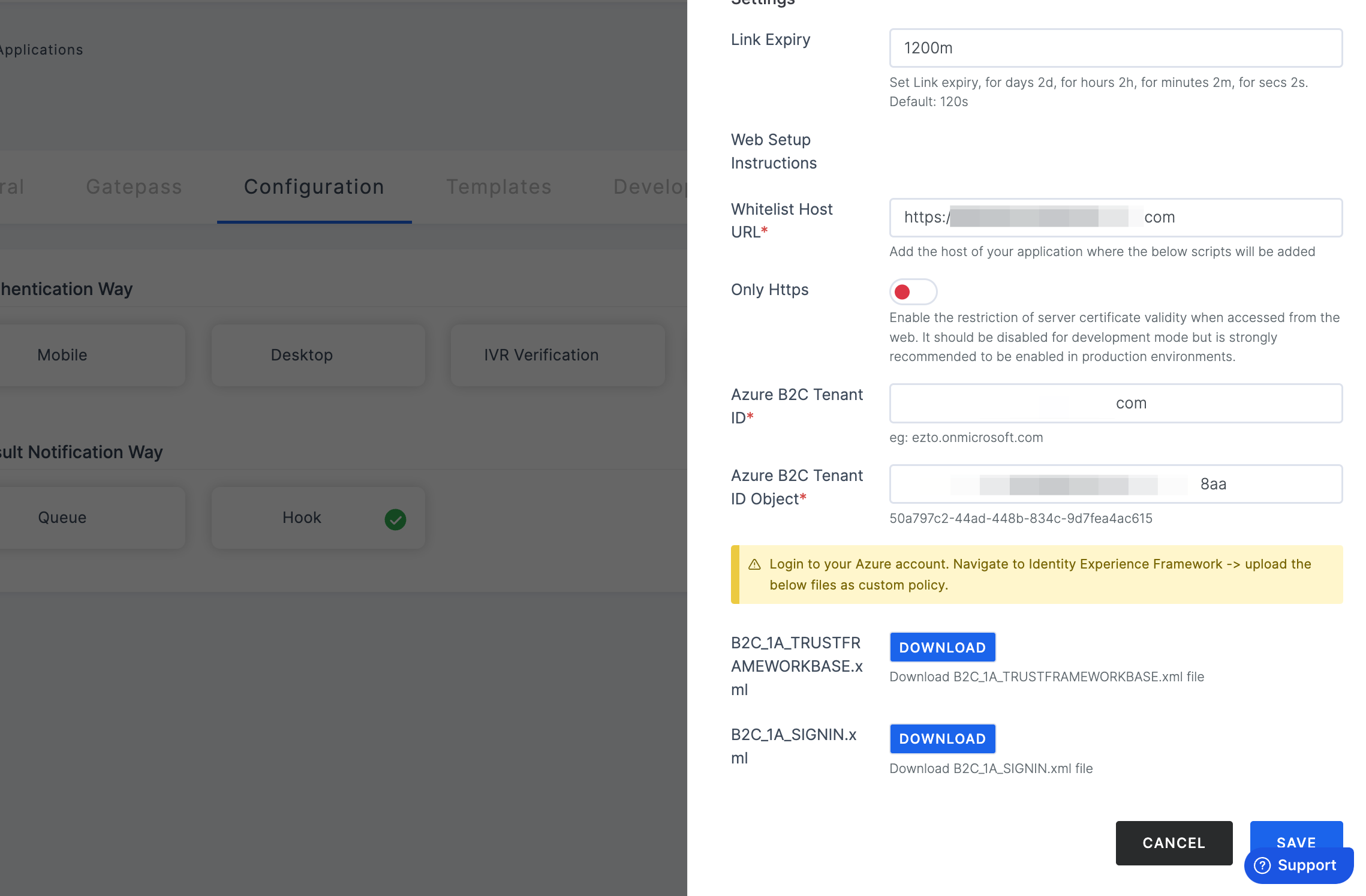
Azure B2C settings
(*) Indicates an action to be mandatory.
| Name | Description |
|---|---|
| Link Expiry | Set the duration after which the link will expire: 2 days (2d), 2 hours (2h), 2 minutes (2m), or 2 seconds (2s). The default is currently set to 120 seconds. |
| Whitelist Host URL | Ensure that the effective URL matches the whitelist URL to prevent unauthorized access. |
| Only Https | Enable or disable server certificate validity restriction when accessed from the web. This is recommended for production environments to ensure secure communication. |
| *Azure B2C Tenant ID | The Azure B2C tenant ID, which follows the format yourtenant.onmicrosoft.com |
| Azure B2C Tenant ID Object | The unique identifier for your Azure B2C tenant object. |
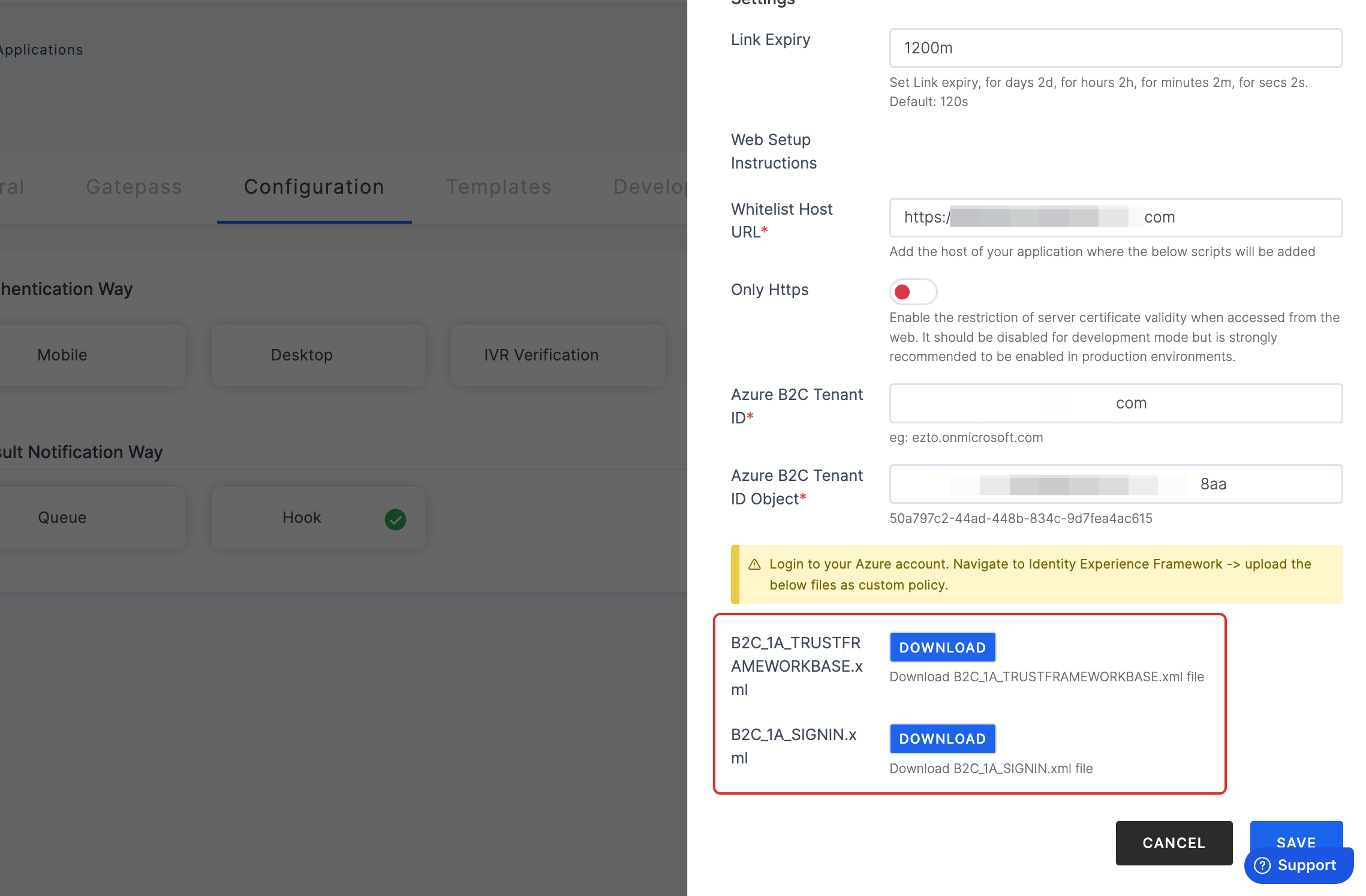
5 Download the B2C_1A_TRUSTFRAMEWORKBASE.xml and B2C_1A_SIGNIN.xml files, and click on the SAVE button.
For Result Notification Way, select Hook, and configure the Hook Notification way as
Web_sdk
Setup Azure B2C
1 Login to your Azure account, go to Identity Experience Framework and click on Upload custom policy.
2 Upload the downloaded XML files.
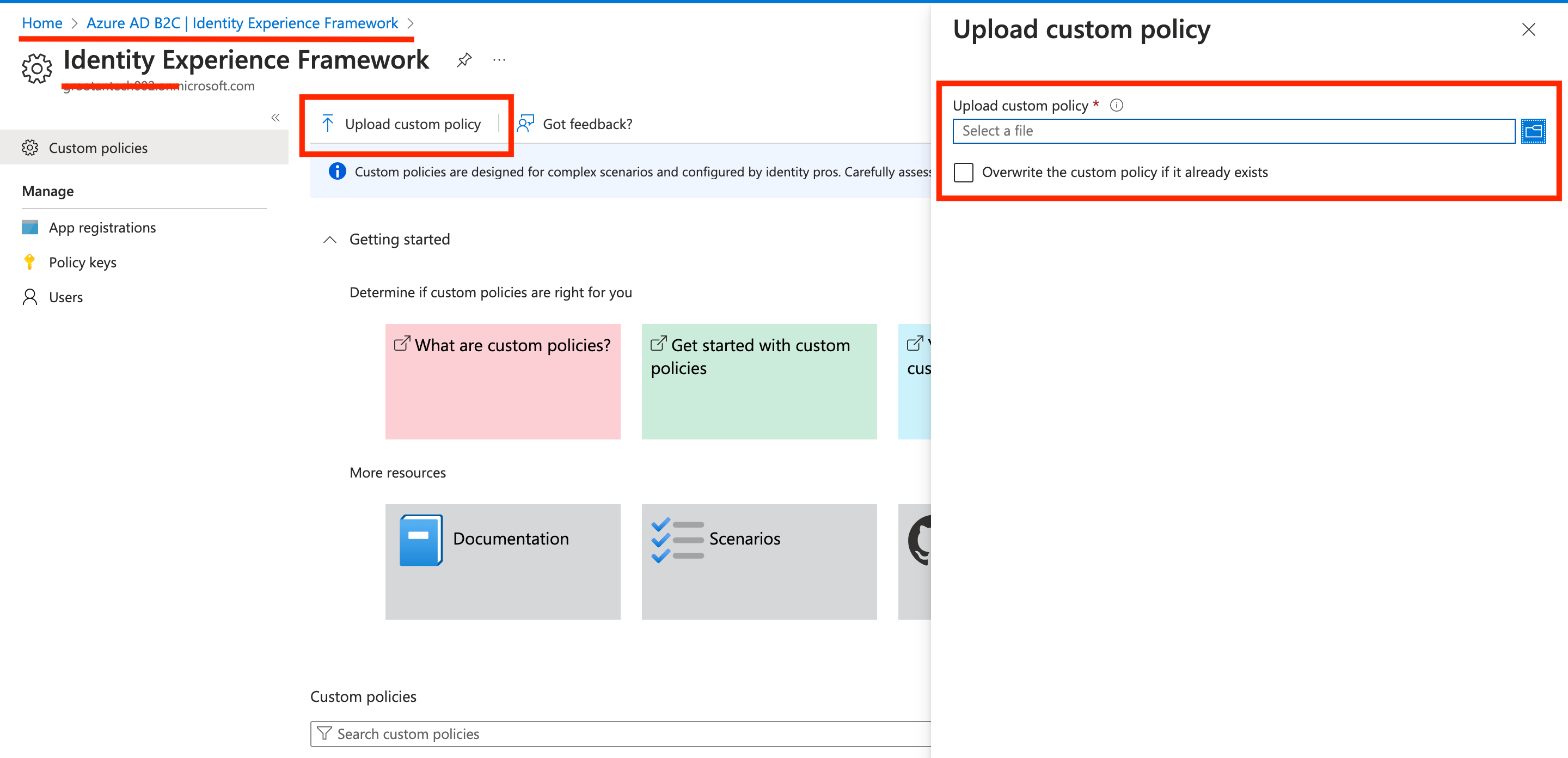
3 In the same page, under Manage, click on Policy keys.
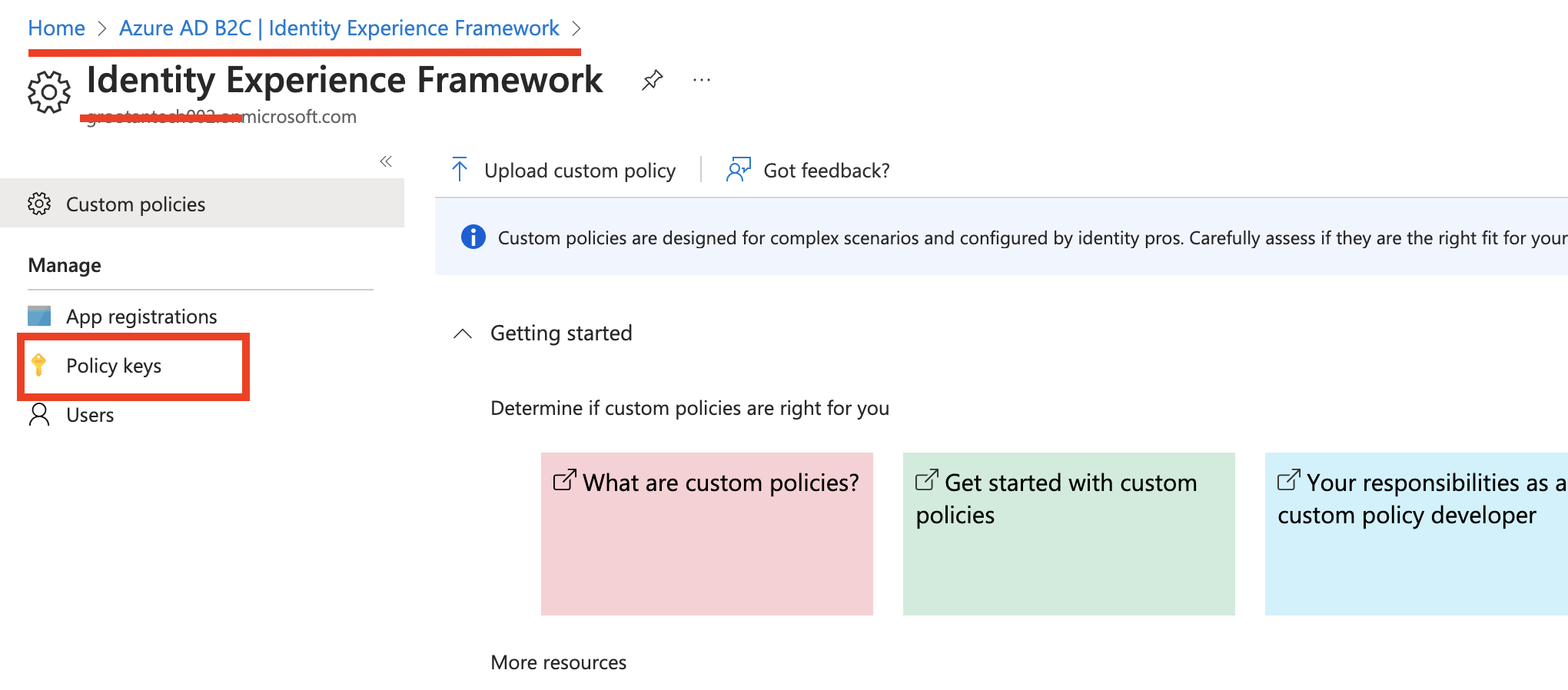
4 Click on the +Add button to generate a signature key named TokenSigningKeyContainer with key type as RSA and key usage as Signature
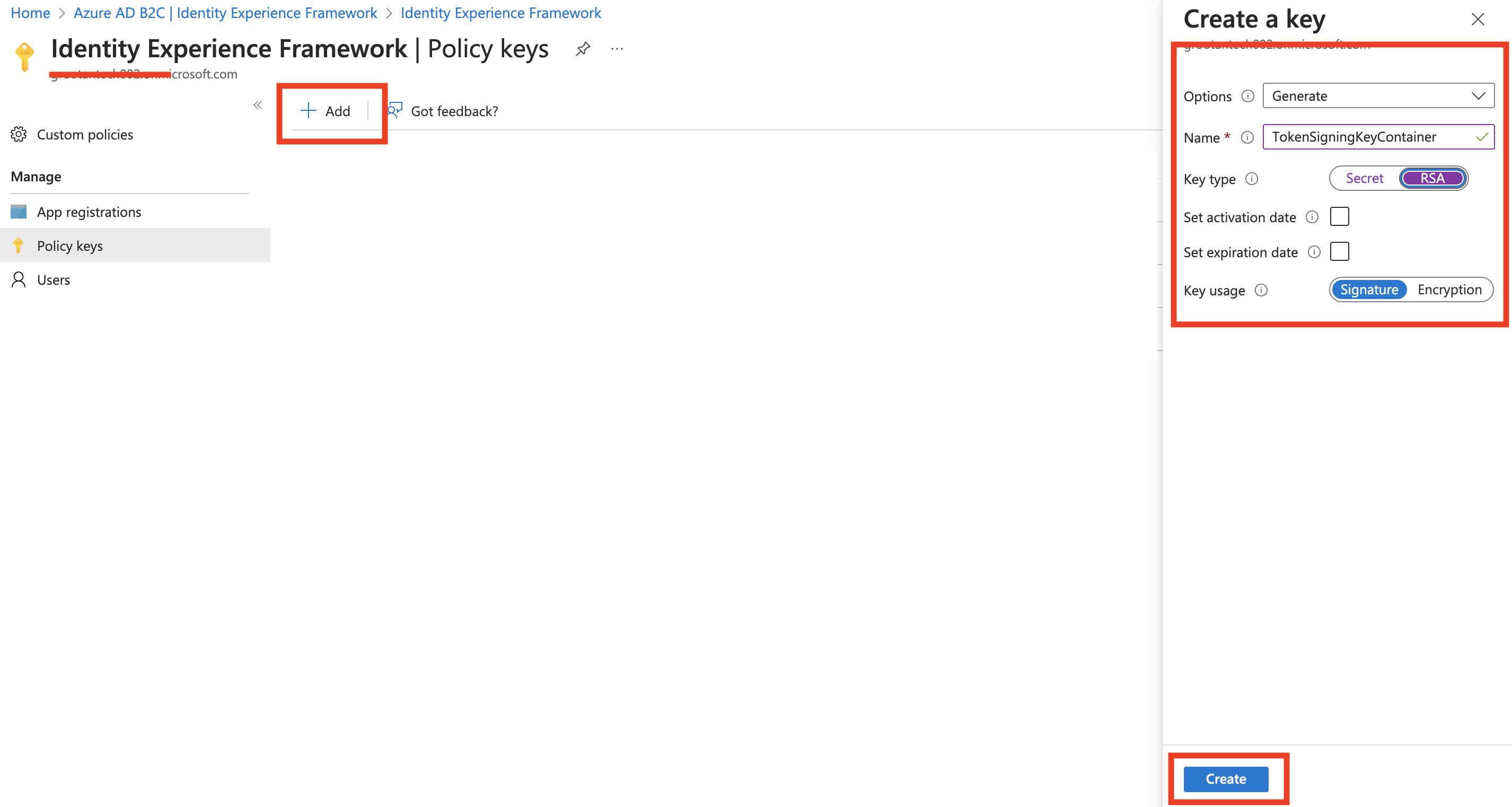
5 The keys will be generated.
The names of the generated keys may differ from those downloaded.

6 To proceed with the sign-in, click on the created key an copy the login endpoint from there.
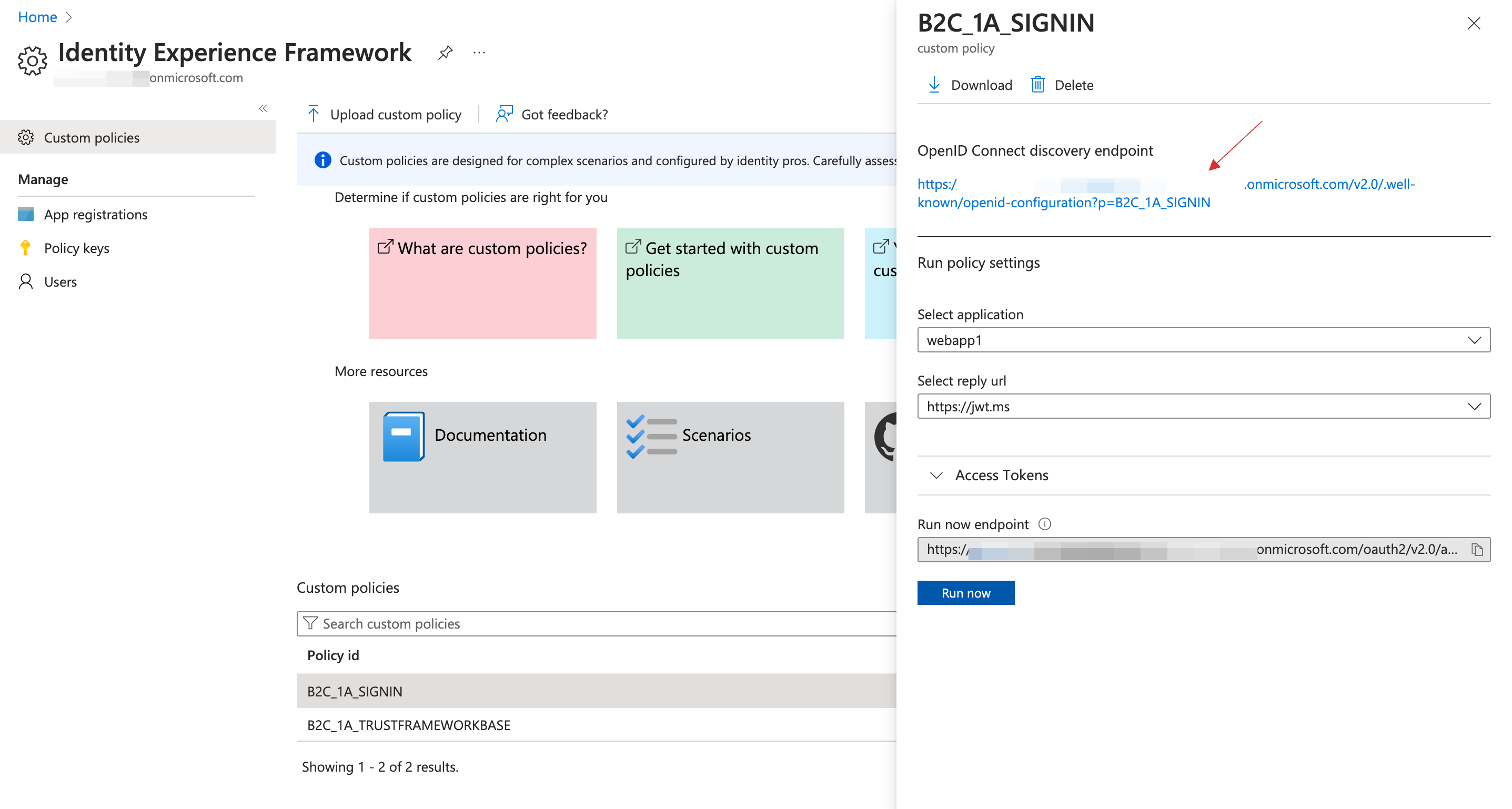
7 Proceed with login using the copied endpoint.
8 The verification flow will be triggered based on the configured workflow.